Cryptocurrency has a number of different problems and one of them is that it’s not even remotely private. Transparency is baked into the system for most coins. Anyone can see what’s happening right now on Bitcoin’s blockchain by going to https://www.blockchain.com/explorer and after a search and a few clicks, you can find out what’s going on in the present block. That anyone could be your nosy neighbour, an authoritarian government or a personal enemy. Literally anyone can see transactions, and with a little technical know-how, even determine who owns the addresses. You can be found.
That’s fine for most folks. The faulty George W. Bush dictum of “You’ve got nothing to worry about if you’ve got nothing to hide” doesn’t send shivers down their spines. Good for them. For the rest of us—there’s privacy coins.
And first among privacy coins is Monero (XMR).
Monero’s protocol is open source and based on CryptoNote, a concept originally devised by anonymous creator Nicolas Van Saberhagen in his 2013 white paper. Monero uses a mix of ring signatures, zero-knowledge proofs and “stealth addresses” to hide transaction details. These features come standard with the coin, but users have options to view keys for third party auditing. Validation happens through a miner network running RandomX, which is a proof of work algorithm. This algorithm issues new coins to miners and is designed to be ASIC resistant.
Monero boasts the third largest development community among cryptocurrencies, only lagging behind bitcoin and Ethereum. Its privacy features have attracted all manner of peculiar malcontent—from cypherpunks (folks advocating for strong cryptography and privacy enhancement tech as a route for political change) and other such privacy advocates. What it’s probably best known for is its use in money laundering, darknet markets, ransomware and cryptojacking. The IRS has multiple bounties out looking for contractors than can find a way to track monero’s movements.
So far? No dice.
How does the privacy function work anyway?
The addresses of monero users are protected using ring signatures, which group a senders address with others. Essentially, a ring signature is a type of digital signature performed by any member of a set of users that each have keys. A message signed with a signature is thereby endorsed by someone in a particular set of people. One of the features of a ring signature is that it’s computationally unfeasible to determine which of the set’s members’ keys was used to produce the signature.
Expand that out to include an entire network and tracking transactions on the Monero blockchain becomes nearly impossible, if not completely impossible. Ring confidential transactions was introduced in 2017 to help hide transactions. Developers also used a zero-knowledge proof method called “Bulletproofs” to guarantee a transaction occurred without shows its value. Last, Monero users are protected through “stealth addresses,” which are generated by users to collect funds, but are untraceable to an owner by anyone observing the network.
The monero protocol also obscures the IP addresses of devices involved in transactions using a method of transaction broadcast propagation. Basically, new transactions are originally passed ot one node on the network, and a repeated probabilistic method determines when the transaction should be sent to one node or sent out to many nodes in a process called flooding. This method was developed to counter the growing blockchain analysis market fostered by companies like Bigg Digital Assets (BIGG.C) and DMG Blockchain Solutions (DMGI.V) blockseer explorer product.
Bad Reputation
Many cryptos come with a bad reputation attached simply because they’re crypto, and most of these aren’t deserving. Monero isn’t one of those. It’s actually earned every bit of bad press it’s gotten because of what it’s been used for in the past. It’s a common medium of exchange on darknet markets. Reuters reported in 2019 that three of the five biggest darknet markets accepted monero, though bitcoin was still the most widely used form of payment in these markets, henceforth proving that criminals are either cocky, dumb or both. See the growing blockchain analysis market companies named above for details.
Then there’s all the cryptojacking.
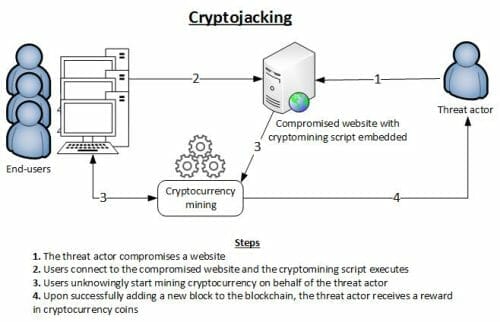
Cryptojacking is when a hacker embeds malware into websites and that can hijack CPU’s to mine monero for them. The biggest and most well known of which is Coinhive, a program embedded in websites and apps that spread like a virus into advertisements and websites, which infected anyone’s computer who visited these sites and used it to mine monero while the visitor was on the site. This is especially insidious because the site owner was often in on the scam, and got a kickback of the minted coins. It was ultimately blocked by companies offering ad blocking subscription lists, antivirus services, and anti-maleware services. Coinhive has even shown up in Showtime-owned streaming platforms. Yes. That Showtime. As well as Starbucks Wi-Fi hotspots in Argentina.
Perhaps there’s a touch of irony in that your computer visits bad porn sites and comes away with an expensive virus. Maybe that’s been a tired joke for awhile and I’m just realizing it now.
Regardless, Monero sometimes gets used in ransomware. In the first half of 2018, monero was used in 44% of ransomware attacks.
The Reaction
Governments react to the behaviours of populations in much the same way parents do to naughty children—by taking away their disruptive toys. In this case, there’s not much legislators and law enforcement can do about decentralized blockchains themselves, so what they do is go after the onramp and offramps. And sometimes the threat of government intervention is enough to scare businesses into regulating their own behaviour. Some exchanges have either dropped or won’t accept Monero because of the inherent threat of regulation.
Exchanges in South Korea and Australia don’t accept it and other privacy coins, making it harder for folks in those countries to exchange their monero for fiat, courtesy of regulatory pressure. There are still ways to do it, naturally—that’s the peculiar thing about any cryptocurrency—you can’t actually stop anything from happening, you just raise the cost of doing so in either opportunity cost or tech requirements. But if you’re savvy and patient enough, you can still do anything.
That’s why Monero will always be around. In 2018, Europol wrote that the year would see criminals shift from using bitcoin to monero, as well as Ethereum, dash and Zcash. We haven’t really seen that in its entirety some three years in because it’s 2021 and Bitcoin is still tops in the underworld, but we wouldn’t and you can’t really prove a negative. Maybe we have?
Where can I get Monero?
At least for right now access isn’t entirely limited.
Despite its reputation there are plenty of places where you can buy and sell monero, including top tier exchanges like Kraken, Binance, Bitfinex and Huobi. Actually, the latest news is that Kraken is going to delist Monero, so maybe the shift is starting.
But honestly even when and if they bow to regulatory pressure, you’ll always have various decentralized exchanges (DEX) of the pop-up weekend variety or the established ones like Uniswap, Sushiswap or PancakeSwap where you’ll likely continue with the option.
The final word on this particular coin isn’t one of discretion. It’s to point out another con with the project. Yes. It provides privacy and privacy provides a certain modicum of security, but what security from peeping neighbours or nosy (or nefarious) governments, it detracts in volatility. This isn’t going to be a problem for most dedicated hodlers, hardened against riding the daily waves of BTC and ETH. The rest of us, though? It represents a significant problem especially if you’re looking to get decent return for your investment.
That’s the price you pay for privacy, though.
—Joseph Morton







One word: Bisq. Try Bisq, an open-source, decentralized platform. Or perhaps BTC/XMR atomic swap?
Or if your risk profile is robust enough – try the Haven Protocol (XHV).
Privacy Stablecoin.